Systems Engineering’s (SE) Lunch & Learn "Information Security Evolution and the Modern Network" was recently held in Bangor and Portland, ME and Nashua, NH. This event covered cybersecurity, its current state, how threat intelligence has grown, and an overview of the evolving layers of security.
Systems Engineering’s (SE) Lunch & Learn "Information Security Evolution and the Modern Network" was recently held in Bangor and Portland, ME and Nashua, NH. This event covered cybersecurity, its current state, how threat intelligence has grown, and an overview of the evolving layers of security.
The lead speaker for the event, Ande Smith, is President of Deer Brook Consulting. Deer Brook provides information security, privacy, and IT consulting services to government and private sector organizations. Smith spoke to the importance of creating and implementing a successful security program, including:
- Taking a comprehensive look at not only your risks and the technolgies you need to keep your organization safe, but also keeping in mind the human factor that all too often can defeat the technology.
- Having a sustainable program. Don’t run out and buy the latest solution. Instead, invest the time in one that will work for your organization for the long term.
- Put thought into how your program will work for not only IT but for everyone in your organization.
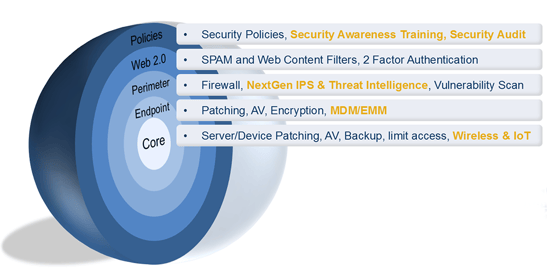
SE’s Product Manager, Mark Benton, followed Smith discussing a few advancements in security technologies. Benton referenced SE’s Layered Approach to Security (diagram below) which details the various areas of security as well as the technologies needed in each layer to properly secure your network. The orange highlighted defense tactics are ones he focused his presentation on, suggesting that if you’re planning your 2016 security budgets, these are ones you might want to consider investing in.
SE's Layered Approach to Security
Perimeter: Next Generation (NextGen) IPS & Threat Intelligence
There have been major advancements in firewall technologies over the past few years including where, when, and how we obtain information on current threats. Firewalls are now smarter, adaptive and can even track what is happening inside your network. However, these are not ‘set-it-and-forget-it’ technologies and for those organizations whose risks do not warrant an advanced firewall, the current batch of Universal Threat Management (UTM) firewalls continue to be a good choice. Key take-away: If your current firewall is five to six years old or more, it’s time to think about upgrading.
Core: Wireless & Internet of Things (IoT)
Wireless has become a critical service. Most organizations want reliable Wi-Fi connectivity secured for their end-users but also available for employee BYOD devices and visitor use. Segmenting the three audiences is a great way to reduce your risk of infection or breach within your organization. In order to easily do this, cloud managed access point’s (AP) are providing the same benefits as on-premise wireless controllers without the high cost of the controller. So, if you’re thinking about upgrading your wireless in 2016, a cloud managed AP solution is a great option.
Endpoint: Enterprise Mobility Management (EMM) / Mobile Device Management (MDM)
Take a moment to review the following questions:- Are your users accessing critical business files via WiFI?
- Is your organization using Office 365?
- Do you need to control internet access?
- Will you be publishing mobile business apps?
- Do you need granular device control?
- Do you own all the devices or are they BYOD?
- Are you concerned about wiping personal data and apps on mobile devices?
Did you answer Yes to any of the questions above? Then consider a MDM/EMM solution.
According to a recent Gartner survey, mobile security has become the number one concern for organizations. While MDM solutions can do a certain amount of device management, sometimes it’s not enough. EMM solutions not only manage devices, they also manage applications and the data on those devices. This allows you to secure corporate data on devices while avoiding the need to completely wipe an employee's personal smart phone or tablet.
Policies: Security Awareness Training & Security Audits
It goes without saying that one of an organization’s biggest security risks is human error which makes employees' annual security awareness training a must. It’s also a compliance risk (HIPAA, GLBA, PCI, etc.). According to Verizon, 11% of end-users click on links in phishing emails. At SE, we see the impact of this on our clients regularly. Even with the best technology, human error accounts for 95% of all successful attacks. Once security awareness training is implemented and reinforced with phishing tests, employees will be up-to-date on the latest scams and have the right reflexes when suspicious emails arrive. In addition, training will save your organization an estimated $180 per employee, far more than the cost of training. Make room in your 2016 budgets for this critical layer of security.
If you are a current client looking for assistance with your 2016 IT budget or to receive more information on any of these security solutions, contact your SE Account Manager, or email info@syseng.com.